編輯:關於Android編程
Android利用Recovery模式,進行恢復出廠設置,全量包OTA升級,增量包升級。
升級一般通過運行升級包中的META-INF/com/google/android/update-script腳本來執行自定義升級,腳本中是一組recovery系統能識別的UI控制,文件系統操作命令,例如write_raw_image(寫FLASH分區),copy_dir(復制目錄)。該包一般被下載至SDCARD和CACHE分區下。
升級中還涉及到包的數字簽名,簽名方式和普通JAR文件簽名差不錯。公鑰會被硬編譯入recovery,編譯時生成在:out/target/product/XX/obj/PACKAGING/ota_keys_inc_intermediates/keys.inc
下面先上圖,說明recovery的總體流程,流程圖繪制了系統從啟動加載bootloader後的行為流程。
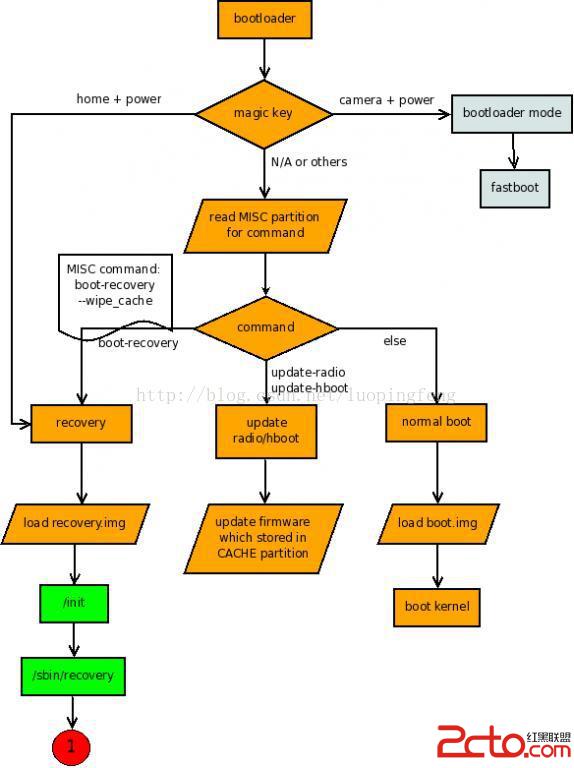
Bootloader正常啟動,有三種方式,按照BCB(Bootloader Control Block)中的command分類:
command == "boot-recovery' → 啟動recovery.img。recovery模式
command == 'update-radio/hboot' → 更新firmware(bootloader)
其他 → 啟動boot.img
Recovery 工具通過NAND cache分區上的三個文件和主系統打交道。主系統(包括恢復出廠設置和OTA升級)可以寫入recovery所需的命令,讀出recovery過程中的LOG和intent。
/cache/recovery/command: recovery命令,由主系統寫入。所有命令如下:
--send_intent=anystring - write the text out to recovery.intent
--update_package=root:path - verify install an OTA package file
--wipe_data - erase user data (and cache), then reboot
--wipe_cache - wipe cache (but not user data), then reboot
/cache/recovery/log:recovery過程日志,由主系統讀出
/cache/recovery/intent:recovery輸出的intent
Bootloader Control Block (BCB) 存放recovery bootloader message。結構如下:
struct bootloader_message {
char command[32];
char recovery[1024];
};
command可以有以下兩個值
“boot-recovery”:標示recovery正在進行,或指示bootloader應該進入recovery mode
“update-hboot/radio”:指示bootloader更新firmware
recovery內容
“recovery\n
其中recovery command為CACHE:/recovery/command命令
用戶選擇“恢復出廠設置”
設置系統將"--wipe_data"命令寫入/cache/recovery/command
系統重啟,並進入recover模式(/sbin/recovery)
get_args() 將 "boot-recovery"和"--wipe_data"寫入BCB
erase_root() 格式化(擦除)DATA分區
erase_root() 格式化(擦除)CACHE分區
finish_recovery() 擦除BCB
重啟系統
升級系統下載 OTA包到/cache/some-filename.zip
升級系統寫入recovery命令"--update_package=CACHE:some-filename.zip"
重啟,並進入recovery模式
get_args() 將"boot-recovery" 和 "--update_package=..." 寫入BCB
install_package() 作升級
finish_recovery() 擦除 BCB
** 如果安裝包失敗 ** prompt_and_wait() 等待用戶操作,選擇ALT+S或ALT+W 升級或恢復出廠設置
main() 調用 maybe_install_firmware_update()
如果包裡有hboot/radio的firmware則繼續,否則返回
將 "boot-recovery" 和 "--wipe_cache" 寫入BCB
將 firmware image寫入cache分區
將 "update-radio/hboot" 和 "--wipe_cache" 寫入BCB
重啟系統
bootloader自身更新firmware
bootloader 將 "boot-recovery" 寫入BCB
erase_root() 擦除CACHE分區
清除 BCB
main() 調用 reboot() 重啟系統
/init → init.rc → /sbin/recovery →
main():recovery.c
ui_init():ui.c [UI initialize]
gr_init():minui/graphics.c [set tty0 to graphic mode, open fb0]
ev_init():minui/events.c [open /dev/input/event*]
res_create_surface:minui/resource.c [create surfaces for all bitmaps used later, include icons, bmps]
create 2 threads: progress/input_thread [create progress show and input event handler thread]
get_args():recovery.c
get_bootloader_message():bootloader.c [read mtdblock0(misc partition) 2nd page for commandline]
check if nand misc partition has boot message. If yes, fill argc/argv.
If no, get arguments from /cache/recovery/command, and fill argc/argv.
set_bootloader_message():bootloader.c [set bootloader message back to mtdblock0]
Parser argv[] filled above
register_update_commands():commands.c [ register all commands with name and hook function ]
registerCommand():commands.c
Register command with name, hook, type, cookie.
Commands, e.g: assert, delete, copy_dir, symlink, write_raw_image.
registerFunction():commands.c
Register function with name, hook, cookie.
Function, e.g: get_mark, matches, getprop, file_contains
install_package():
translate_root_path():roots.c [ "SYSTEM:lib" and turns it into a string like "/system/lib", translate the updater.zip path ]
mzOpenZipArchive():zip.c [ open updater.zip file (uncompass) ]
handle_update_package():install.c
verify_jar_signature():verifier.c [ verify signature with keys.inc key; verify manifest and zip package archive ]
verifySignature() [ verify the signature file: CERT.sf/rsa. ]
digestEntry():verifier.c [ get SHA-1 digest of CERT.sf file ]
RSA_verify(public key:keys.inc, signature:CERT.rsa, CERT.sf's digest):libc/rsa.c [ Verify a 2048 bit RSA PKCS1.5 signature against an expected SHA-1 hash. Use public key to decrypt the CERT.rsa to get original SHA digest, then compare to digest of CERT.sf ]
verifyManifest() [ Get manifest SHA1-Digest from CERT.sf. Then do digest to MANIFEST.MF. Compare them ]
verifyArchive() [ verify all the files in update.zip with digest listed in MANIFEST.MF ]
find_update_script():install.c [ find META-INF/com/google/android/update-script updater script ]
handle_update_script():install.c [ read cmds from script file, and do parser, exec ]
parseAmendScript():amend.c [ call yyparse() to parse to command ]
exeCommandList():install.c
exeCommand():execute.c [ call command hook function ]
erase DATA/CACHE partition
prompt_and_wait():recovery.c [ wait for user input: 1) reboot 2) update.zip 3) wipe data ]
ui_key_xxx get ALT+x keys
1) do nothing
2) install_package('SDCARD:update.zip')
3) erase_root() → format_root_device() DATA/CACHE
may_install_firmware_update():firmware.c [ remember_firmware_update() is called by write_hboot/radio_image command, it stores the bootloader image to CACHE partition, and write update-hboot/radio command to MISC partition for bootloader message to let bootloader update itself after reboot ]
set_bootloader_message()
write_update_for_bootloader():bootloader.c [ write firmware image into CACHE partition with update_header, busyimage and failimage ]
finish_recovery():recovery.c [ clear the recovery command and prepare to boot a (hopefully working) system, copy our log file to cache as well (for the system to read), and record any intent we were asked to communicate back to the system. ]
reboot()
 android網絡框架OkHttp之get請求(源碼初識)
android網絡框架OkHttp之get請求(源碼初識)
概括OkHttp現在很火呀。於是上個星期就一直在學習OkHttp框架,雖然說起來已經有點晚上手了,貌似是2013年就推出了。但是現在它版本更加穩定了呀。這不,說著說著,O
 Android WebView使用(一)
Android WebView使用(一)
前言Android內置webkit內核的高性能浏覽器,而WebView則是在這個基礎上進行封裝後的一個 控件,WebView直譯網頁視圖,我們可以簡單的看作一個可以嵌套到
 android webview與js交互(動態添加js)
android webview與js交互(動態添加js)
1、本地html與本地html裡的js交互2、本地html與本地js交互3、網絡html與網絡js交互4、網絡html與本地js交互5、各個情況動態添加js以上5點都可以
 探究startActivityForResult在singleTop和singleTask啟動模式討論
探究startActivityForResult在singleTop和singleTask啟動模式討論
最近在研究AMS代碼遇到一個問題,在函數startActivityUncheckedLocked中 Slog.d("DDY", "!!